Setting up an IDCS Client App for Oracle Content Managements REST API Authentication

If you don't have SSO enabled on you OCM instance you will need to setup an Identity Cloud Service client application that will enable you to authenticate and receive an oAUTH2 token for requests against the OCM REST API.
I've setup an example on the OCM-Social-Widget in github that shows you how to authenticate and use the token to make calls against the OCM API here
Overview
In this guide we'll go through step by step on how to create and connect up the IDCS client app to our OCM instance. The official detailed guide can be found here https://docs.oracle.com/en/cloud/paas/content-cloud/solutions/integrate-oracle-content-management-using-oauth.html#GUID-AC061A7E-6488-4BCB-AAB6-C9928AF23EE0
For this walkthrough - we are going to setup and connect using the Client Credentials Grant type.
IDCS Setup
A few quick steps we will fly through on setting up the client app.
- Login to IDCS Create an Application
- Configure Grant type
- Add the right scope
- Assign application toles
...Let's begin
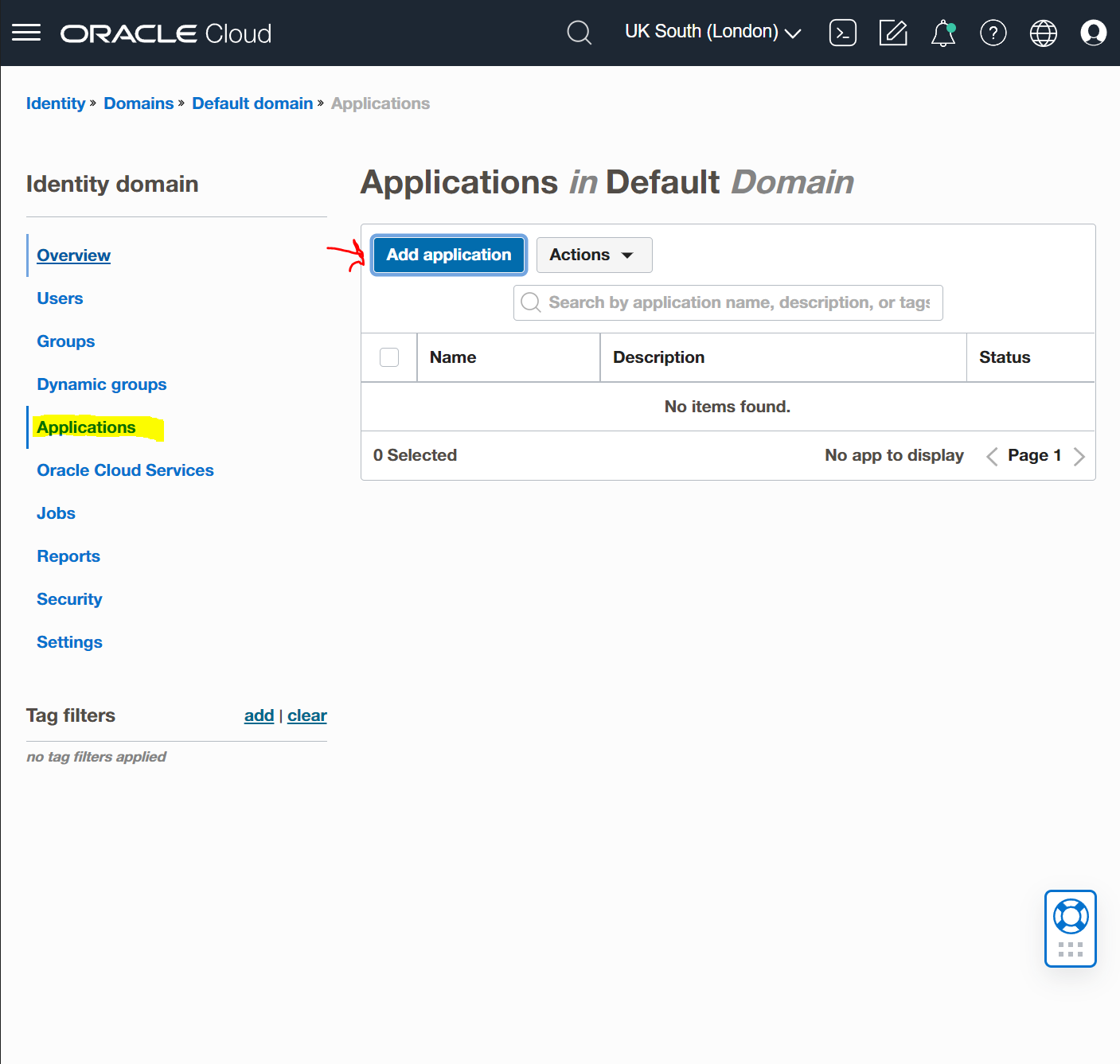
Go into your domains and under "Applications" select the "Add application" button.
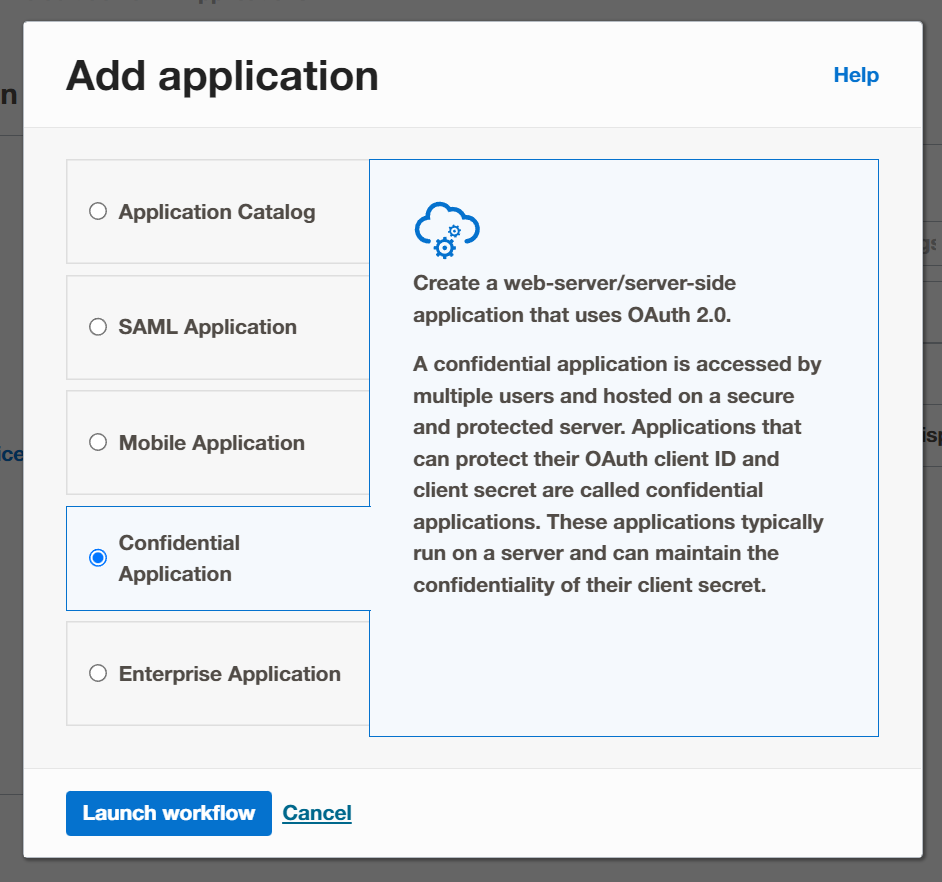
Select the "Confidential Application" and launch into the workflow.
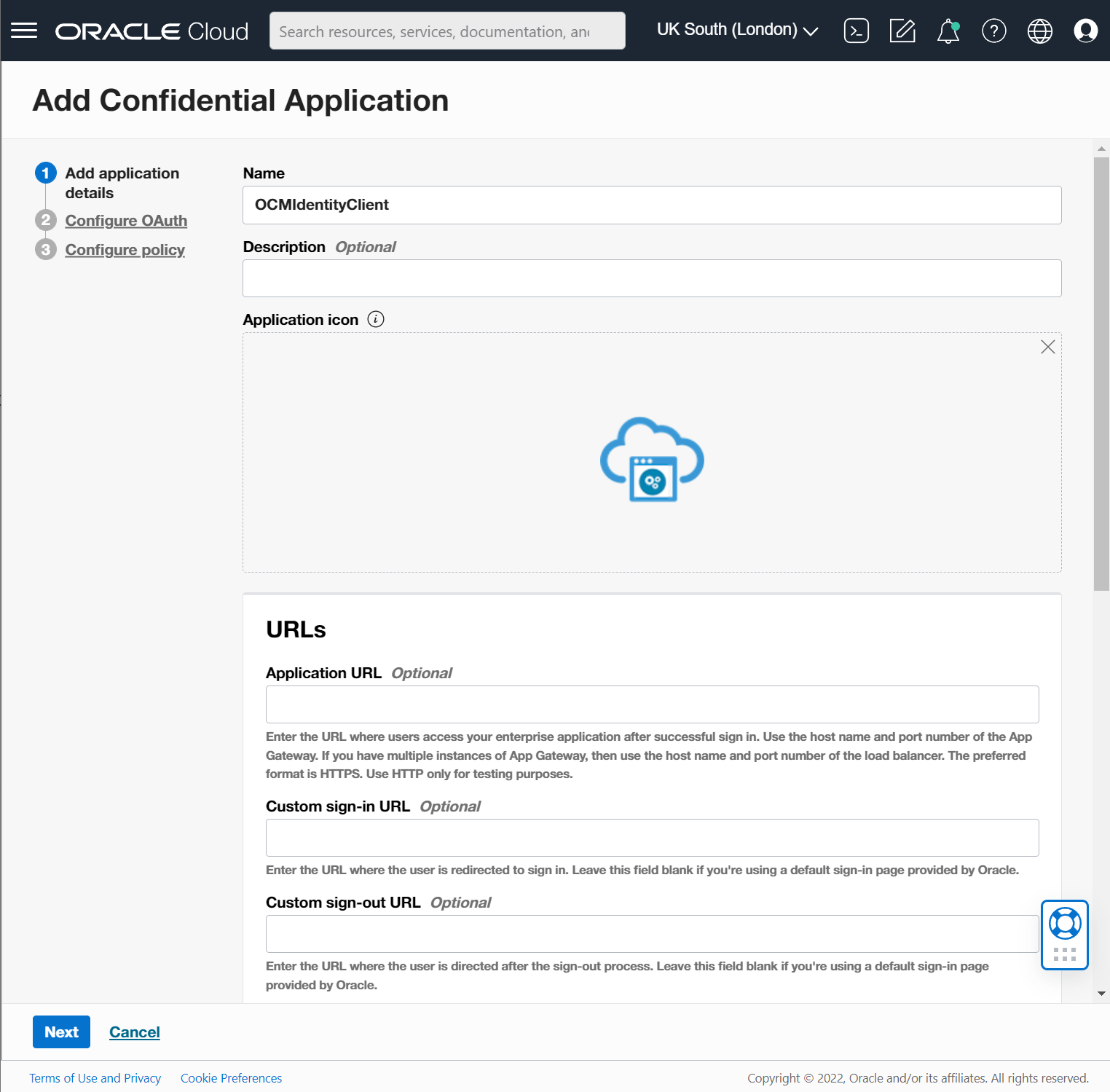
Add name to your new Client app and click next leave all the default settings.
In step2 "Configure OAuth" Select "Configure this application as a client now" and choose "Client credentials". You could also add Resource Owner.
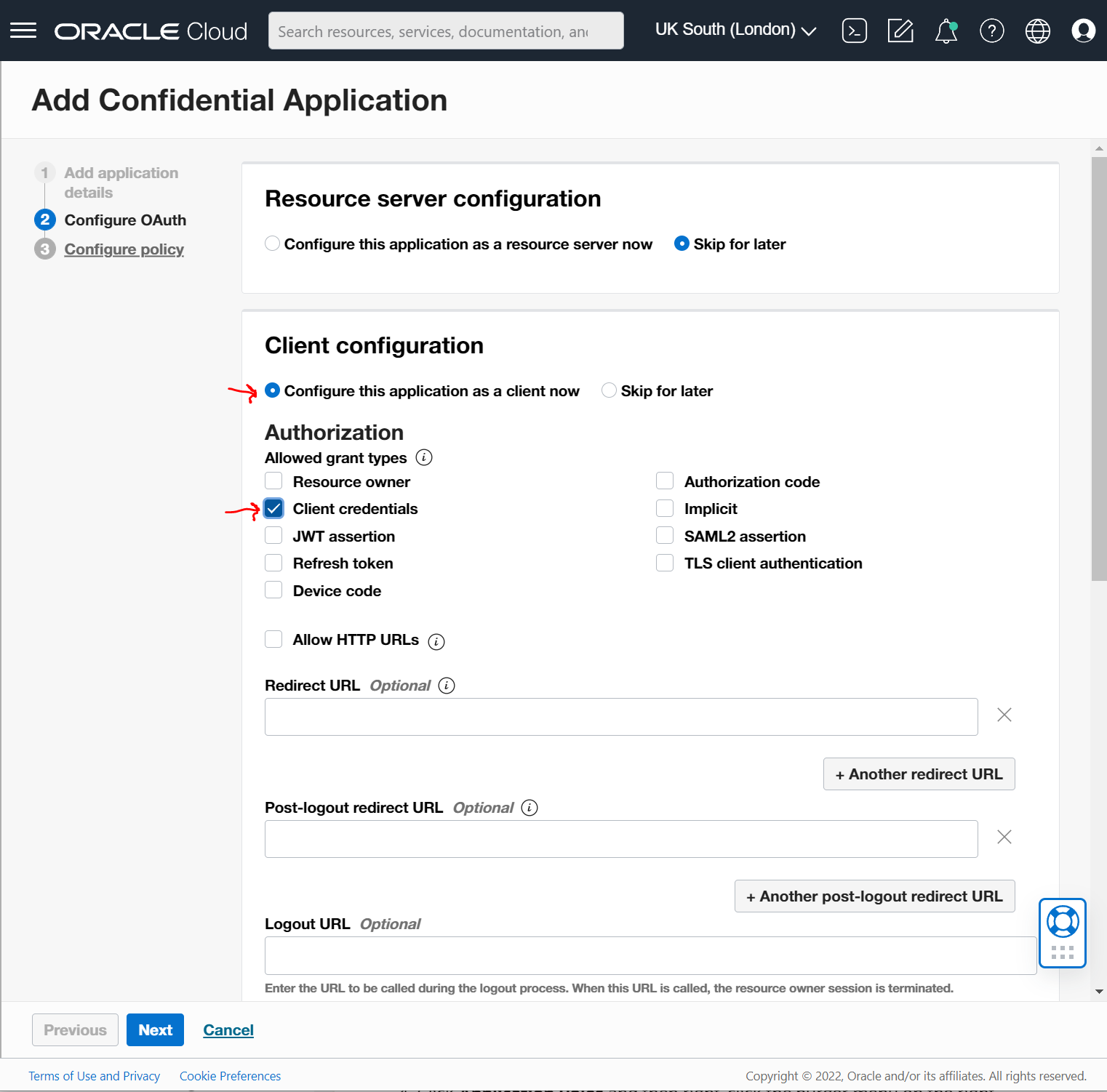
Scroll down and select the "Add resources" checkbox and then go ahead and select the "Add scope" button.
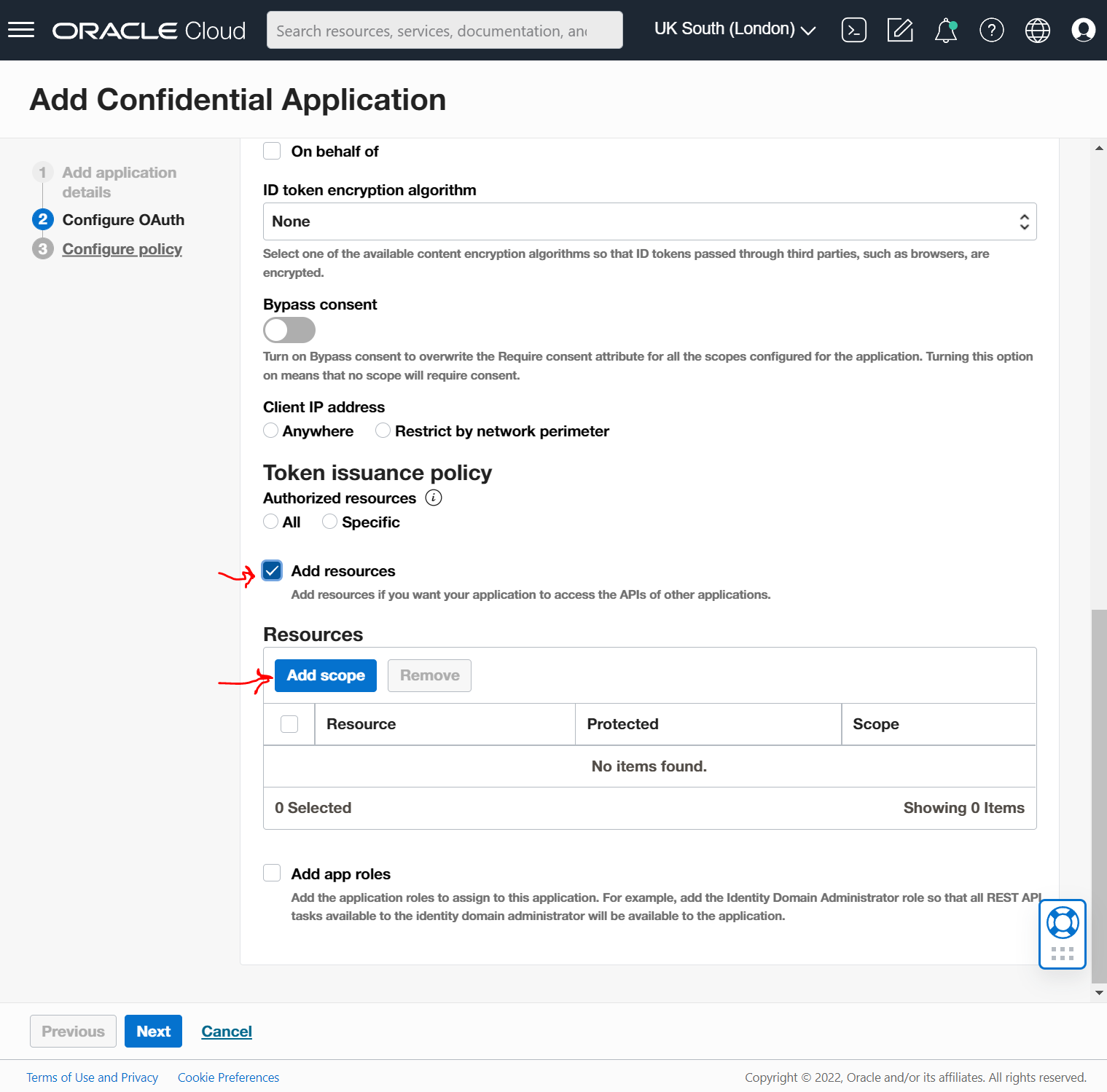
Find your OCM Instance in the list and expand out and find the url ending with "urn:opc:cec:all" check it and select the "Add" button below.
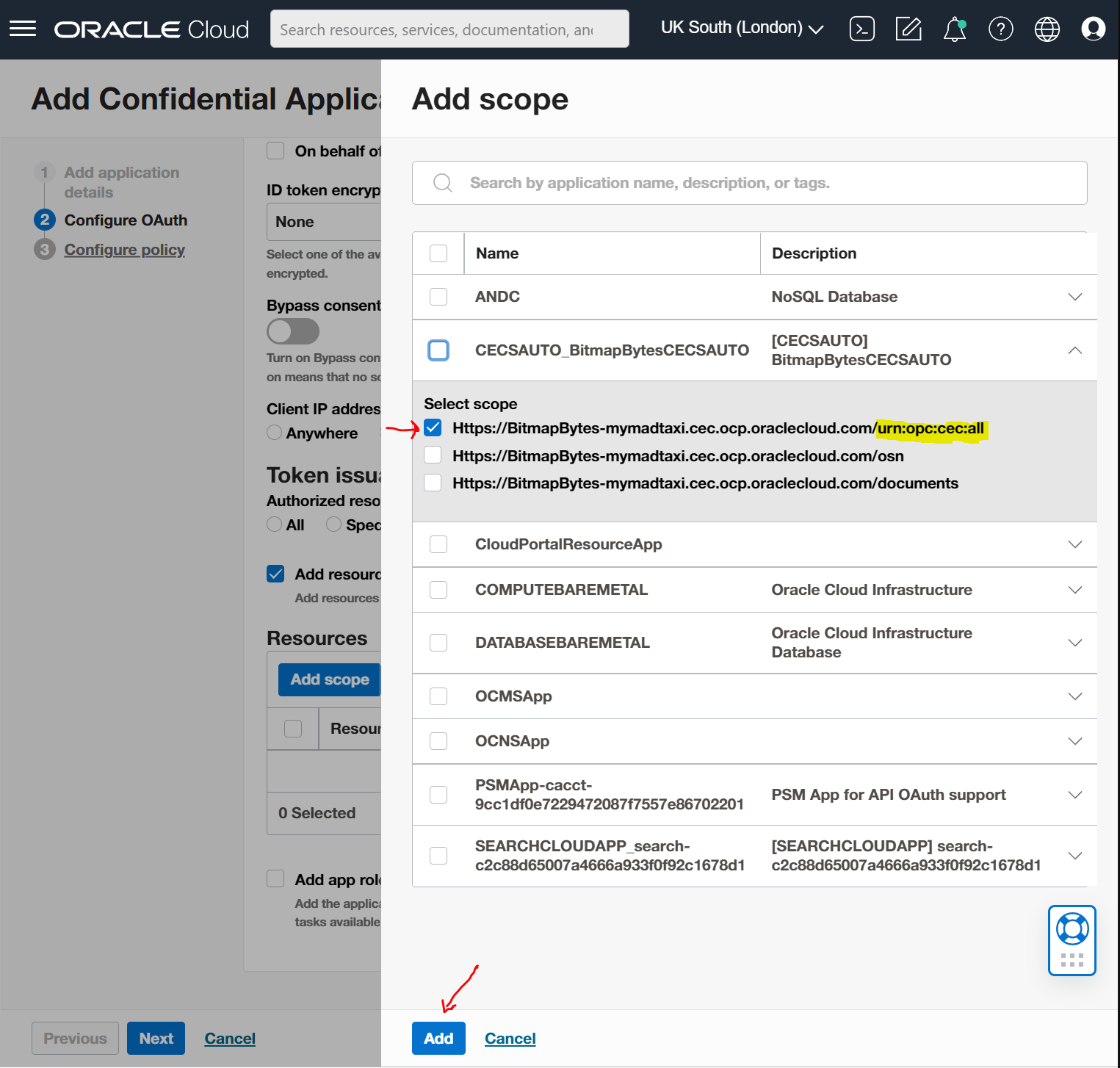
Select the "Finish" button.
Now open up your "Oracle Cloud Services" and select your OCM service usually it's prefixed with "CECSAUTO_".
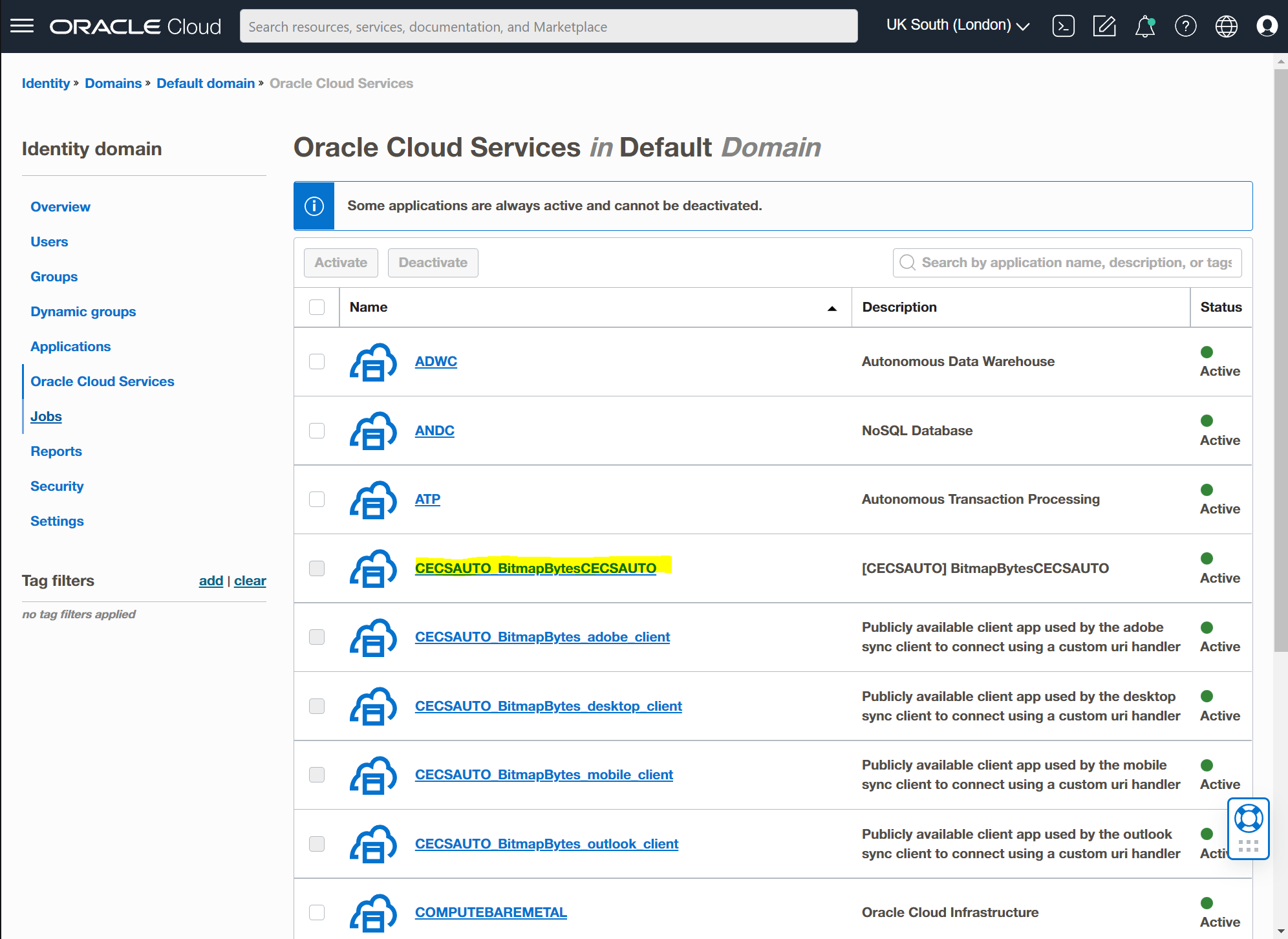
Select your "Application Roles":
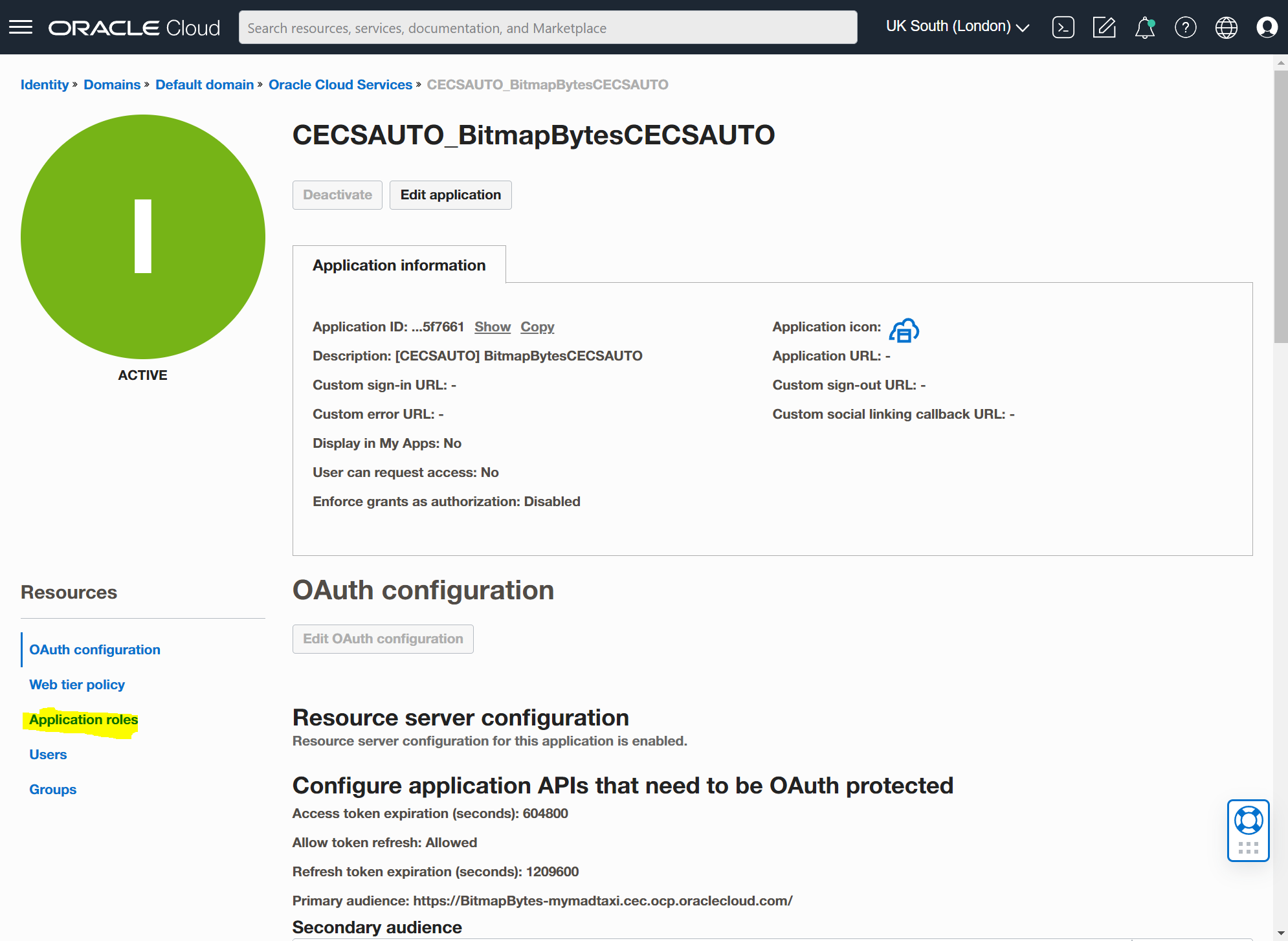
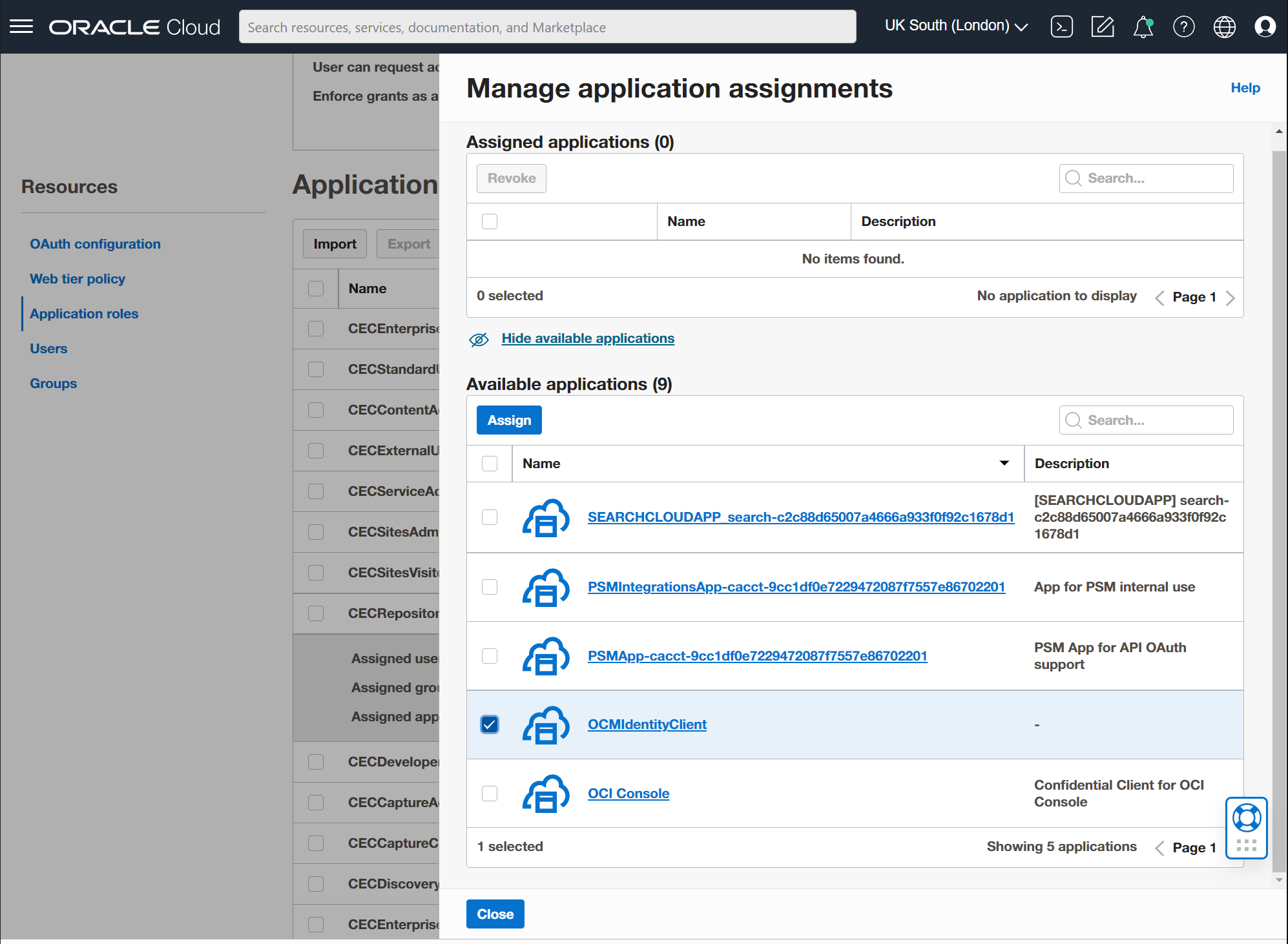
Find "CECRepositoryAdministrator" and expand it with the small arrow on the right. Then select the "Manage" Assigned applications link.
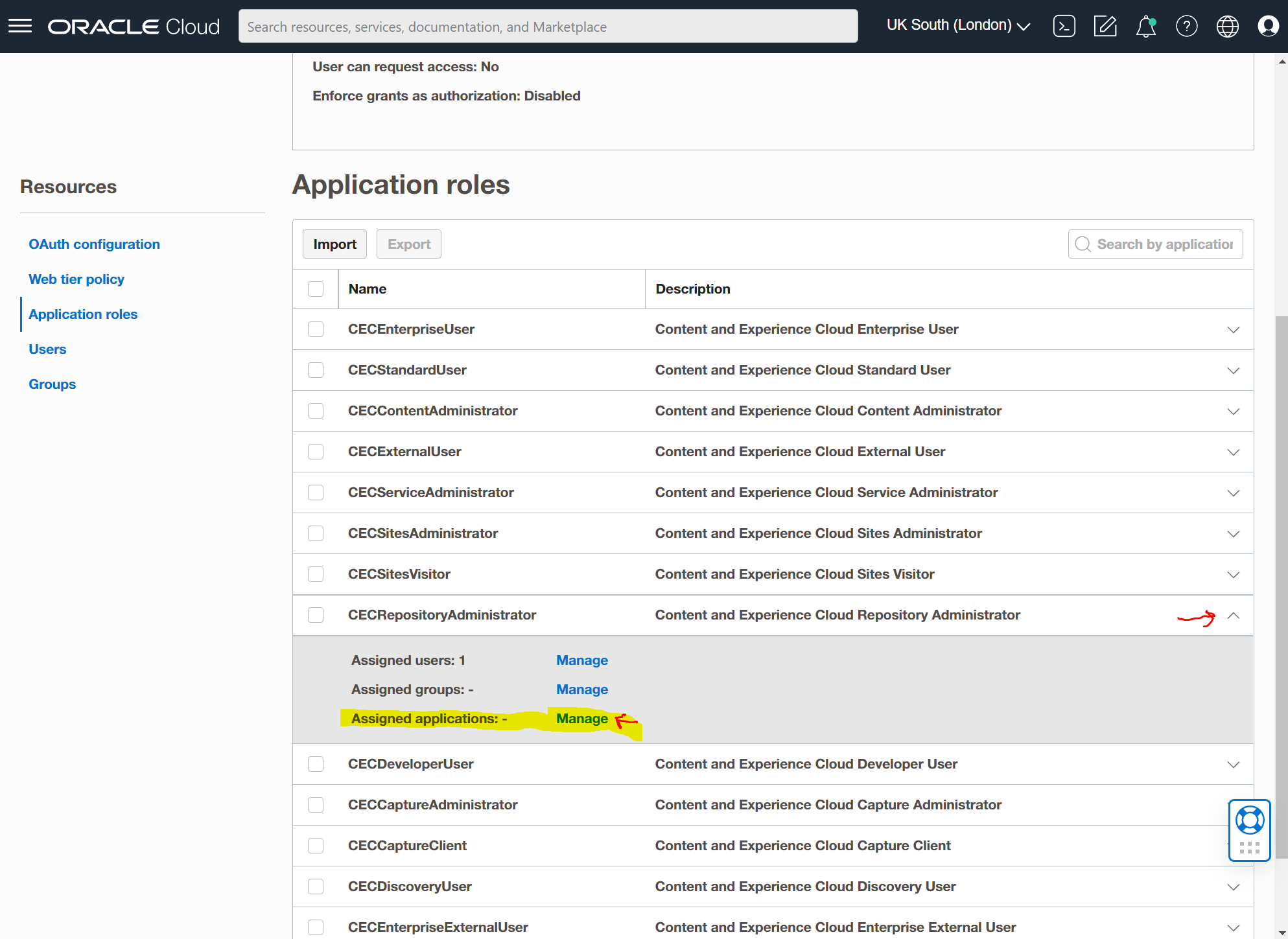
Select the "Show available applications" link.
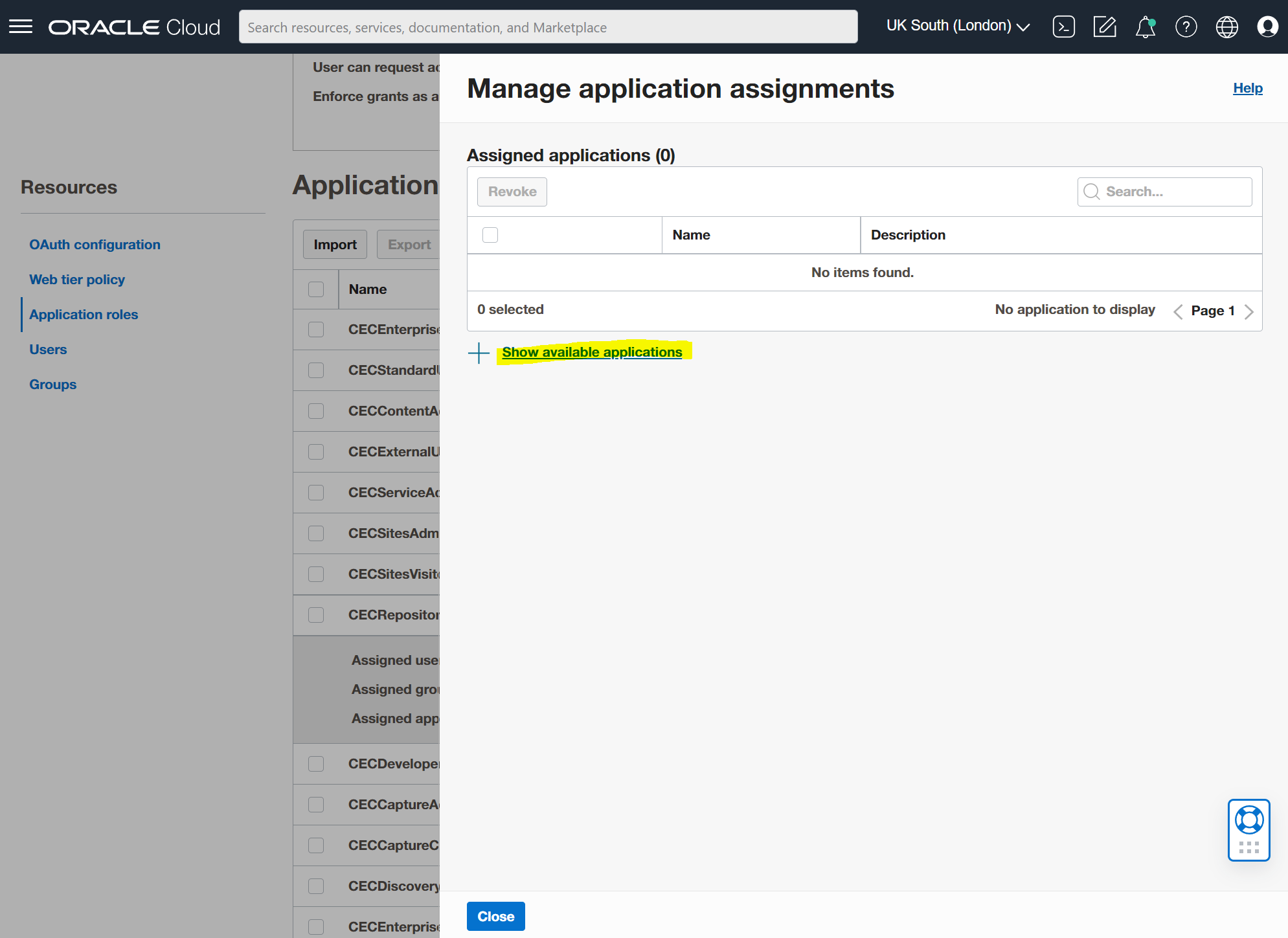
Select the client app you created and the "Assign" button and then the "Close" button. Make you you triple check at this point that it has been successfully assigned.
That should be it...
Testing
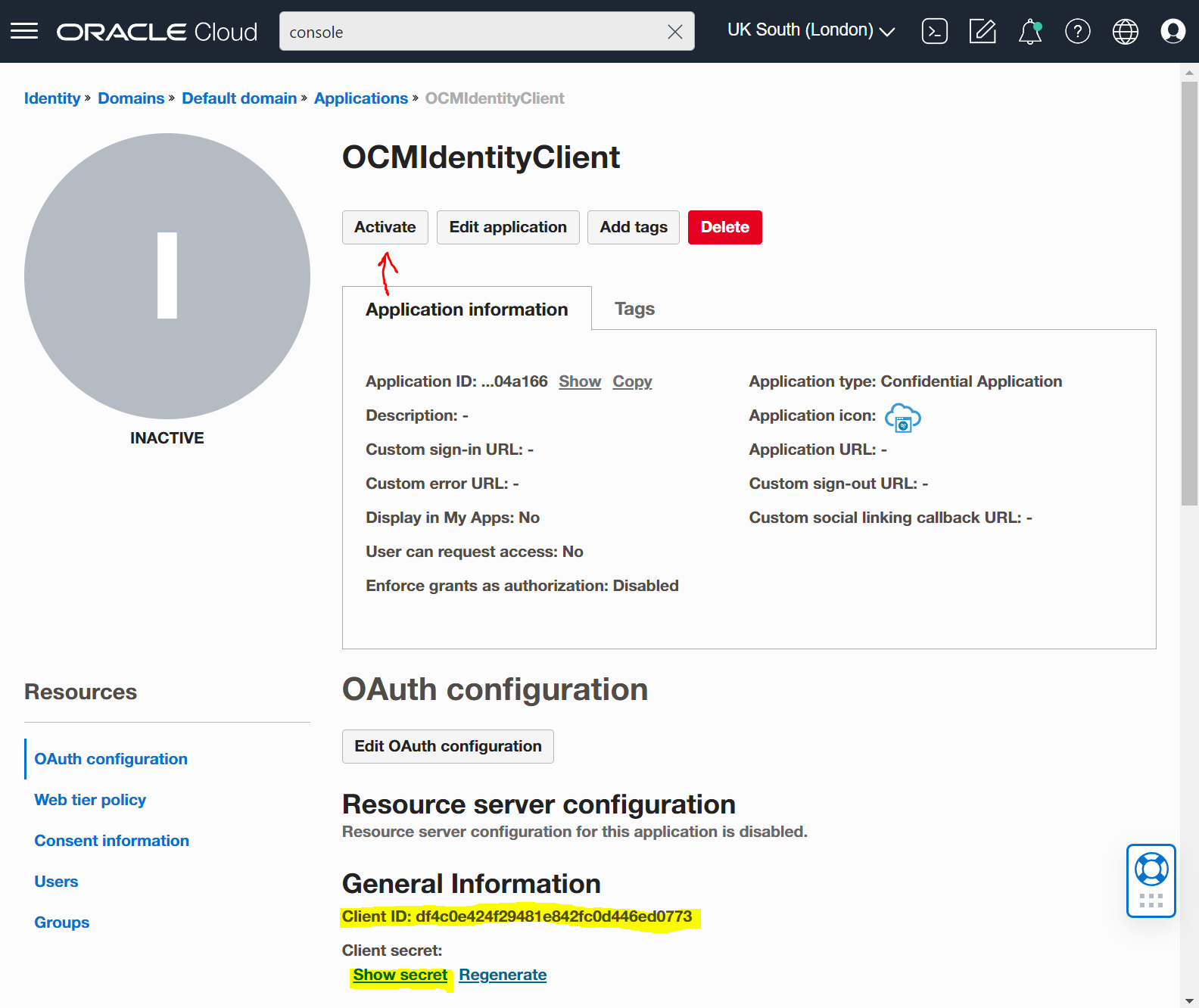
Head over to the client application and copy the
- "Client ID"
- "Client Secret"
- "Scope URL" ending in "urn:opc:cec:all"
Finally check and make sure the app is activated!
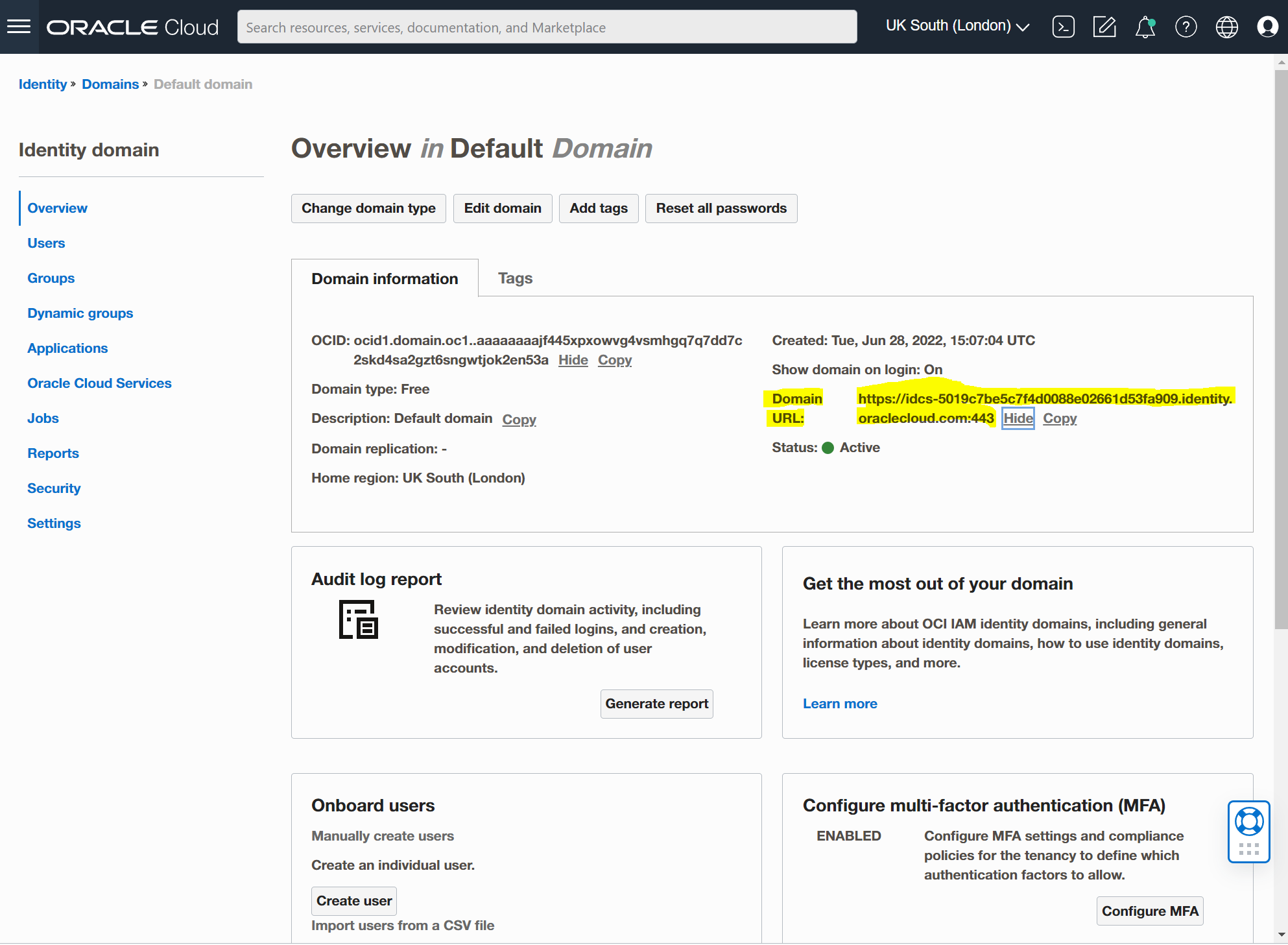
Next go to your Identity Domain and copy and save the Domain URL.
Here is a sample curl command you can use to test out your access..
curl -X POST \
https://<identityDomainURL>/oauth2/v1/token \
-H 'Authorization: Basic <Base64 encoded clientID:clientSecret>' \
-d 'grant_type=client_credentials&scope=<scope string>'If everything was setup successfully you should get the following response.
{"access_token":"<access-token-value>}"You can now use the "<access-token-value>" for OCM API requests with the header authorization bearer token passed across.
curl -X GET <Oracle-Content-Management-URL>/sites/management/api/v1/sites \
-H 'Authorization: Bearer <access-token-value>'\
-H 'Content-Type: application/json'Demo (0%...)
I'll setup a demo this week on github showing sample code and connection to my OCM Free instance. In the meantime you can checkout the OCM-Social-Widget repo that uses the same approach.
